Setup the Touchstone – Tap a Phone – Escalate Privileges & Go
Touchstone makes the principle of least privilege simple to enforce by granting access only when and where it’s needed based on the specific device tapped and who tapped it. For operators, it’s seamless: just tap and go. For owners, it’s precise, dynamic control without the overhead.
Touchstone uses NFC to deliver a single use magic link to the phone. Our service authenticates the provided credentials and redirects the user to the destination specified by the owner and is provided with a one-time code. The owner validates the incoming request and code then uses additional vectors such as user identity to grant access appropriately.

Authorization with presence and intent
Touchstones add a powerful layer of security by tying digital access to physical presence and operator intent. Unlike other authentication methods that rely solely on identity based credentials, Touchstone requires a deliberate, physical tap by the operator ensuring they are not only authorized, but also present and actively choosing to engage. This approach helps prevent unauthorized or accidental access, making it especially effective in dynamic manufacturing environments where tools, documents, and AI systems must be tightly controlled.
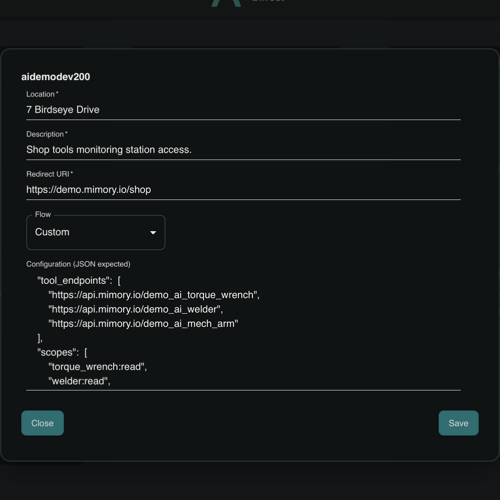
Configurable validation response
When a Touchstone is tapped, it generates a secure, customizable validation response that can serve as a powerful trigger for dynamic access control. The response always includes core data such as the request timestamp, device ID, and a one-time code. Owners can enrich it with metadata like physical location and a custom JSON bucket specific to each Touchstone. This allows the response to integrate seamlessly with existing systems, enabling automatic, temporary adjustments to access permissions based on real-world context. Whether it’s unlocking a machine, surfacing a relevant document, or activating an AI assistant, Touchstones turn a simple tap into a context-aware access event.
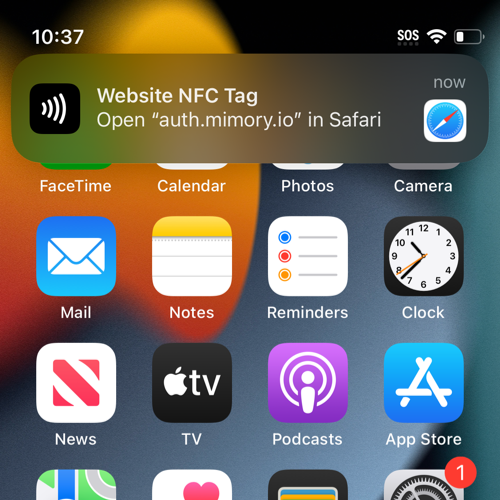
Mobile First
Touchstone is built mobile-first to help factories take full advantage of the next generation of productivity tools. With smartphones, AR glasses, and AI-enabled devices becoming the new standard, mobile platforms offer faster, more effective ways to interact with equipment and information. Touchstone supports this shift by providing secure, presence-based access through the mobile devices your team already uses unlocking new levels of efficiency while keeping you in control.
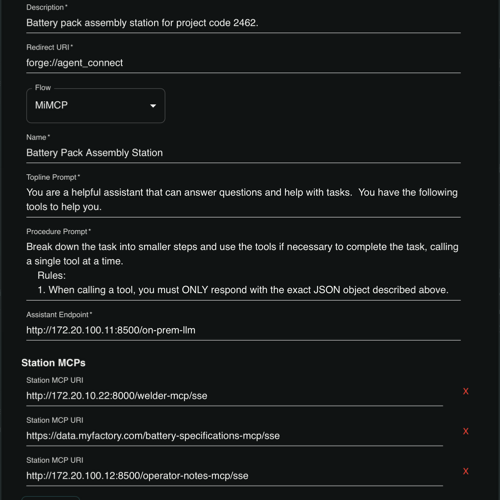
Designed for the age of AI
Touchstone is built for the age of AI, making the mobile device the central connection point where all parts of your system come together. With a simple tap, Touchstone can help connect on-premises AI agents and Model Context Protocol servers to configure machines or assist operators in real time through a conversational interface. All data flows through the mobile device, which acts as the bridge between protected tools, local telemetry, and external services. This design gives you full control over where AI inference happens and ensures seamless, secure interaction across your entire factory setup.
Key Features
Automating Permissions
Touchstone dynamically adjusts access rights based on who’s tapping, where, and when—no manual updates required.
Tools on Tap
Instantly launch apps, surface documents, or trigger AI agents. Touchstone connects operators to the right tools with a single tap.
Modular & Scalable
Deploy a single Touchstone or a fleet, each one is configurable to fit your workflow, from small stations to full-scale lines.
Physical Access Required
Access is only granted through an intentional, in-person tap, ensuring real-world presence and reducing exposure.
